Get Started
Graphite's supplier management tool helps you onboard faster, cut time on risk reviews and streamline supplier validations. Save time and money.
May 9 2023
How to Use a Supplier Risk Assessment Matrix
As your business grows, it’s exposed to various risks that can significantly affect operations and financial stability. That’s why it’s essential to measure supplier risk as a part of risk management in procurement, as it helps mitigate potential threats to your organization.
But, how do you go about measuring different types of supplier risks? And, how do you quantify those supplier risks, so that you can prioritize in order of severity? The answer is the supplier risk matrix.
What Is Risk Management and How is it Related to the Supplier Risk Matrix?
Risk management is the process of identifying, assessing, and mitigating risks to an organization’s assets and resources. The relationship between risk management and the supplier risk matrix is simply that risk matrices are used to identify and rate threats that can then be mitigated by careful management.
What are the Different Types of Supplier Risks
The first stage in this complex process is defining the different types of supplier risks. Aaron Oyler, Chief Product Officer of Graphite, says, “Knowing the risk is out there is one thing, but identifying where that risk is located is quite another.”
Risk identification involves recognizing all possible hazards to your organization’s assets and resources, both internal and external. Inherent risk refers to the probability and impact of an adverse event occurring without any risk management efforts. In contrast, residual risk refers to the probability and impact of an adverse event after considering existing risk management measures.
Different types of risks can pose a threat to your business. Examples of these risks include financial, such as credit and liquidity risks; operational, such as fraud and system failures; strategic, such as competitor threats and market changes; and compliance, such as regulatory and legal changes. By identifying these risks, you can better evaluate your organization’s potential exposure and develop strategies to manage them effectively.
Here are the types of risks that businesses may be exposed to:
1. Core business risks –
These are the inherent threats to the nature of the business, such as operational, financial, and strategic risks.
2. Regulatory risks –
These risks arise due to non-compliance with industry laws and regulations.
3. Industry-related risks –
These risks arise due to factors such as economic conditions, market trends, and competition.
Measure and Place Threats into the Supplier Risk Matrix
It’s essential to have a structured approach when creating a risk register. The risk register is a document that lists all identified risks, their probability of occurring, their potential impact, and measures taken to manage them. Each risk in the register needs an owner responsible for managing it (see the example below).
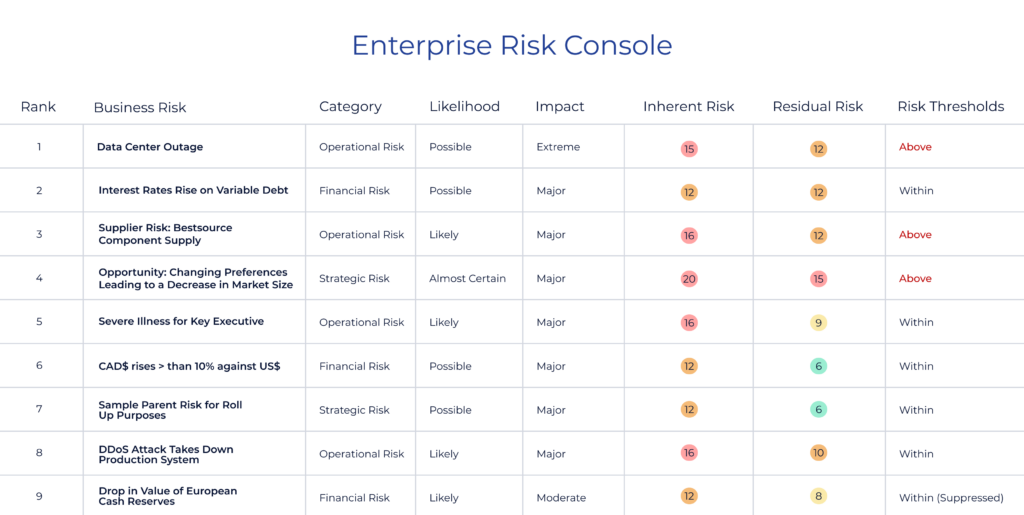
Leveraging a supplier risk matrix can help you rate each risk consistently. A matrix is a tool that evaluates the probability of a risk occurring and its potential consequences. Assigning a score to each risk on the supplier risk matrix allows you to prioritize and determine which risks require immediate attention (see probability and impact matrix below).
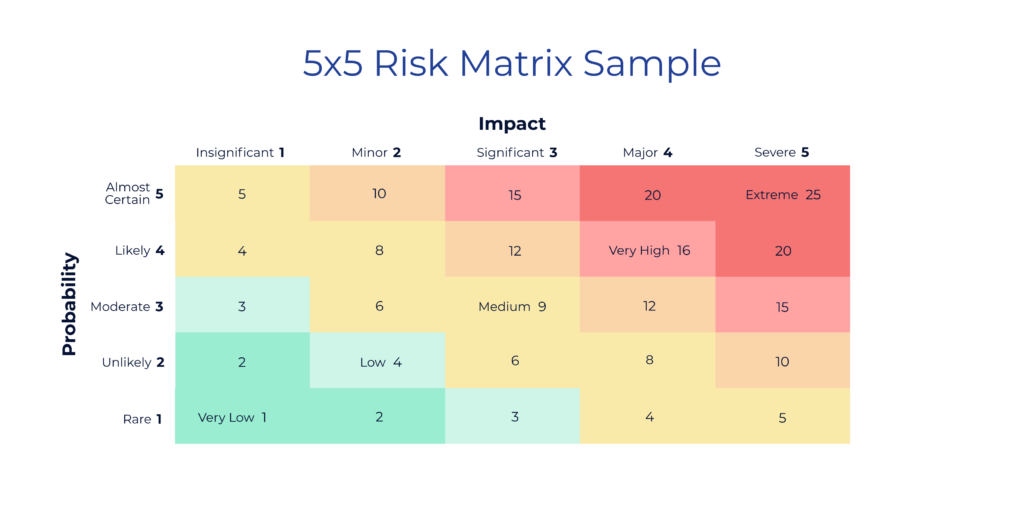
By defining and measure risk, you’ll be better able to mitigate potential threats to your company. But effective risk management doesn’t end there. Once you’ve identified and rated your risks based on their potential impact and likelihood, you’ll want to develop effective management strategies for each one.
Want to know more?
Read our e-book to learn how to build a more robust risk management process that protects your assets and minimizes your organization’s exposure to potential threats.
Read the Ebook